Formidable Tips About How To Avoid Ip Spoofing

These tools mask your ip address and encrypt the data that arrives and leaves your computer or mobile phone.
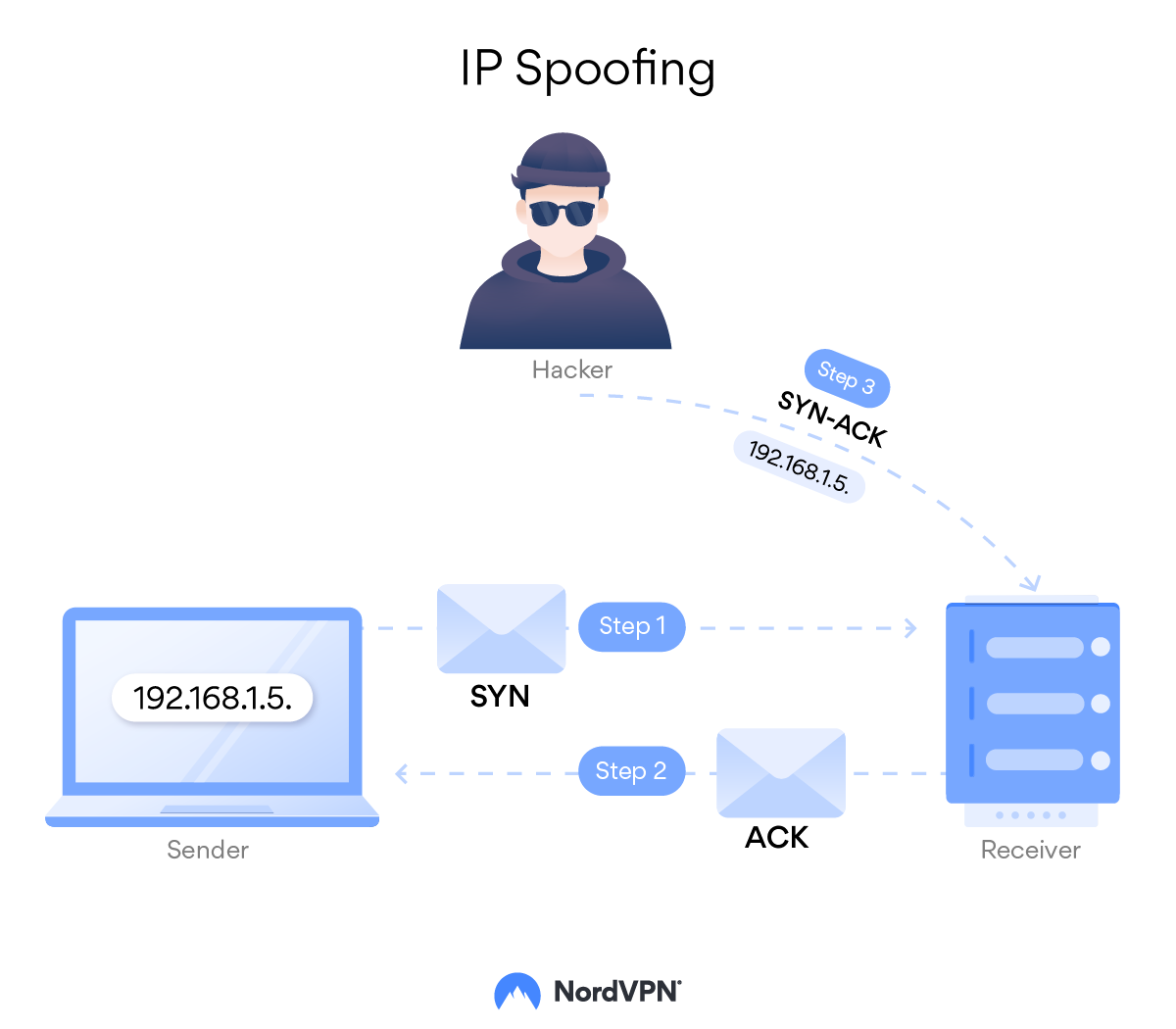
How to avoid ip spoofing. How to protect against ip spoofing? Use strong verification and authentication methods for all remote access. Organizations can take a number of steps to prevent faked packets from infiltrating their networks, including:
Another effective way to prevent ip spoofing involves configuring routers and switches to deny them entry to packets from outside your local network. Most ip methods on how to avoid ip spoofing must be developed and implemented by it professionals who are familiar with computer spoofing. Get in the habit of hiding your ip address when surfing the web to prevent ip spoofing.
It's a good idea to use a network attack blocker. Constantly monitor networks for unusual activity; Deploying packet filtering to detect inconsistencies (such as outgoing.
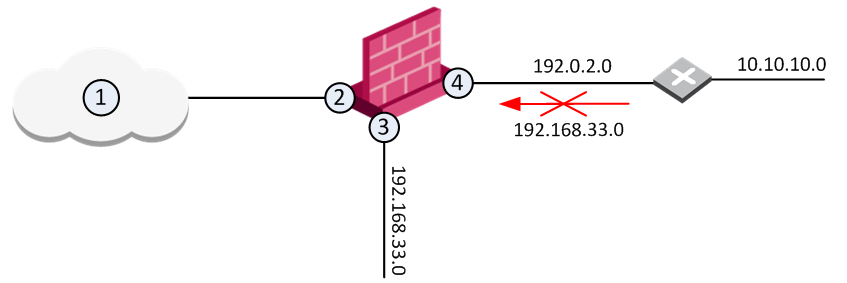
Packet filtering can help to combat ip spoofing attempts. Another way to avoid ip spoofing is by ensuring that your website uses ssl certificates. Packet filtering / ingress filtering.
Up to 20% cash back the options to protect against ip spoofing include: The options to protect against ip spoofing include monitoring networks for atypical activity, deploying packet filtering to detect inconsistencies (like outgoing packets with source ip addresses that don't match those on the organization's network), using robust verification methods (even among networked computers), authenticating all ip addresses, and using a. Cyber attacks cost businesses an average of $200,000 per incident.
Up to 30% cash back hide your ip address: Do not authenticate devices and users solely. How to protect against ip spoofing?
Networks are being monitored for unusual activities. Every device or user attempting to join a network has its ip packets examined. This makes packet sniffing or sequence number analysis much, much harder.
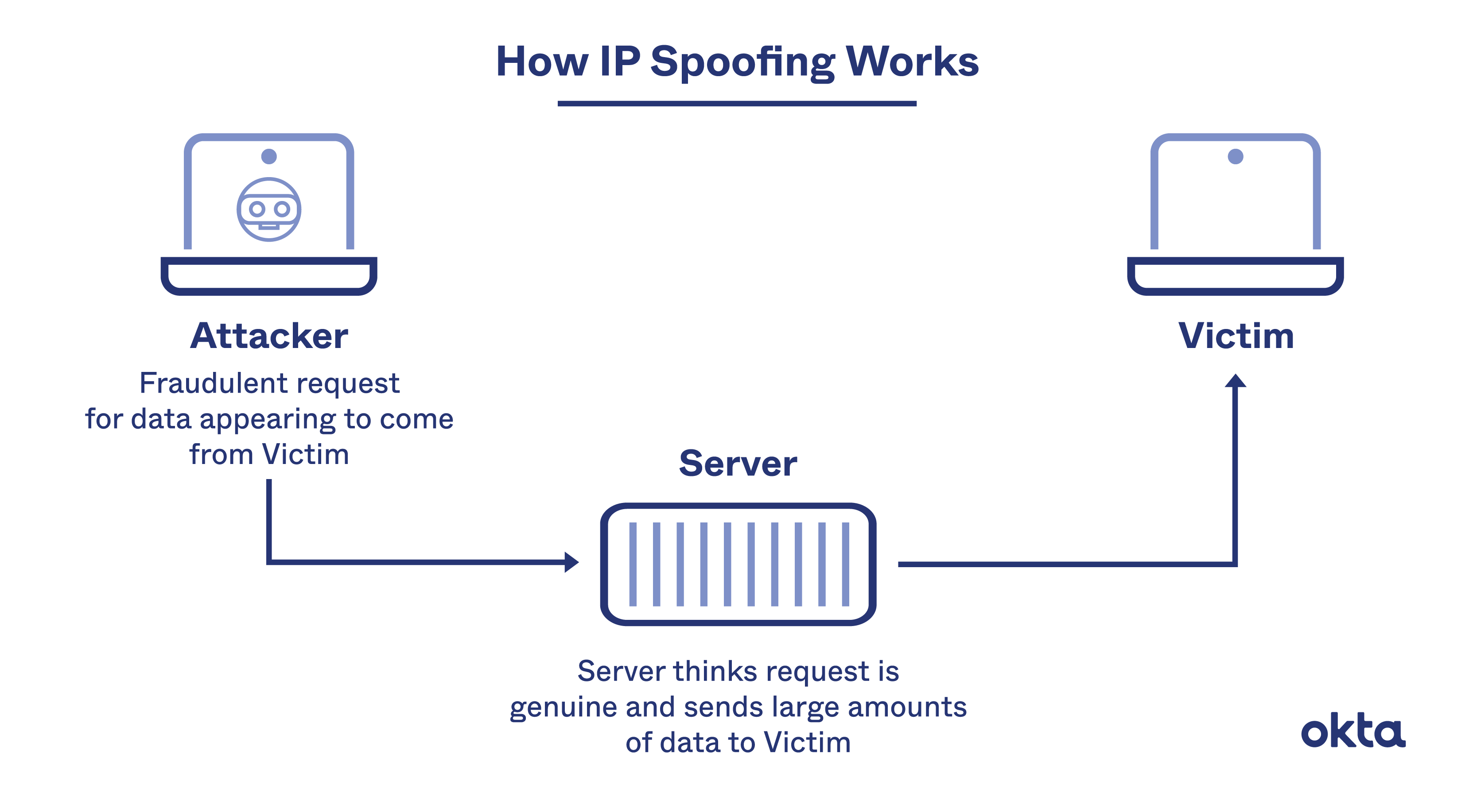
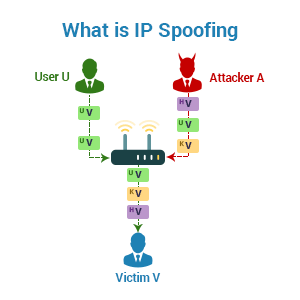
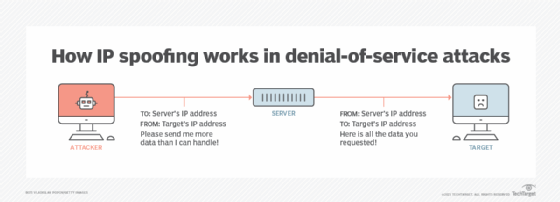
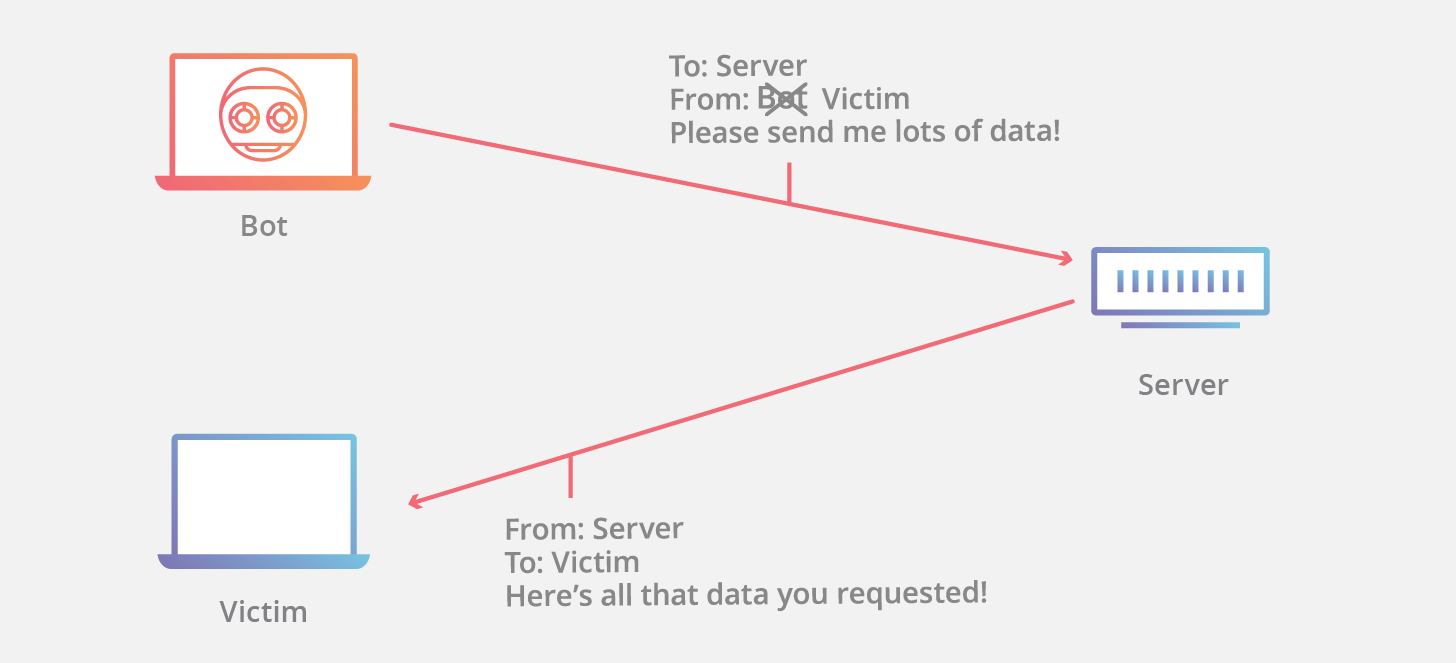
Web designers advocate for the conversion of websites to ipv6. By adding encryption and authentication mechanisms, ipv6. Spoofing is a cyberattack that occurs when a scammer is disguised as a trusted source to gain access to important data or information.
Since ip spoofing is one of the most accessible attacks and one of the most destructive, protecting the. Monitoring networks for atypical activity. Ssl certificates verify that the website is connecting to your network.
Every device or user attempting to join a network has its ip packets examined. Make an acl of ip. Then, monitor your network for suspicious activity with a firewall, which uses a packet filter that inspects ip packet headers.